Google Disrupted One of the World's Largest Residential Proxy Networks. What Every Data Team Needs to Know
On January 28, 2026, Google Threat Intelligence Group, working with Cloudflare, Spur, and Lumen's Black Lotus Labs, disrupted IPIDEA, believed to be one of the largest residential proxy networks in the world.

Gunnar
Last updated -
Feb 11, 2026
Why Hype Proxies
The operation removed millions of devices from the network (with initial estimates suggesting the disruption could impact up to 9 million) and seized dozens of domains. It also exposed a business model few proxy buyers had scrutinized: a significant portion of the "residential proxy" market was running on compromised consumer devices, malware-embedded SDKs, and infrastructure actively used by state-backed threat actors from China, Russia, Iran, and North Korea.
If your team buys proxy services for data collection, scraping, or market research, the mechanics of this operation are worth understanding.
Key takeaways
Google disrupted IPIDEA on January 28, 2026, removing up to 9 million compromised devices from the network and seizing dozens of domains.
IPIDEA operated at least 13 proxy and VPN brands through a single China-based group incorporated through Hong Kong entities.
4 SDKs (software development kits) silently converted consumer devices into proxy exit nodes without user consent.
550+ tracked threat groups, including APT28, Sandworm, and Volt Typhoon, routed through IPIDEA infrastructure in a single 7-day window.
The network directly enabled 3 major botnets: BadBox 2.0, Aisuru, and Kimwolf.
Proxy buyers can independently verify IP sourcing using fraud scoring, reverse DNS, ASN verification, and geolocation testing.
What was IPIDEA?
IPIDEA presented itself as a premium residential proxy provider. The website advertised 6.1 million daily updated IP addresses and 69,000 new IPs rotating in every day.
In practice, IPIDEA ran a network of compromised consumer devices. Phones, tablets, and TV set-top boxes were enrolled as proxy exit nodes, typically without the device owner's knowledge or consent.
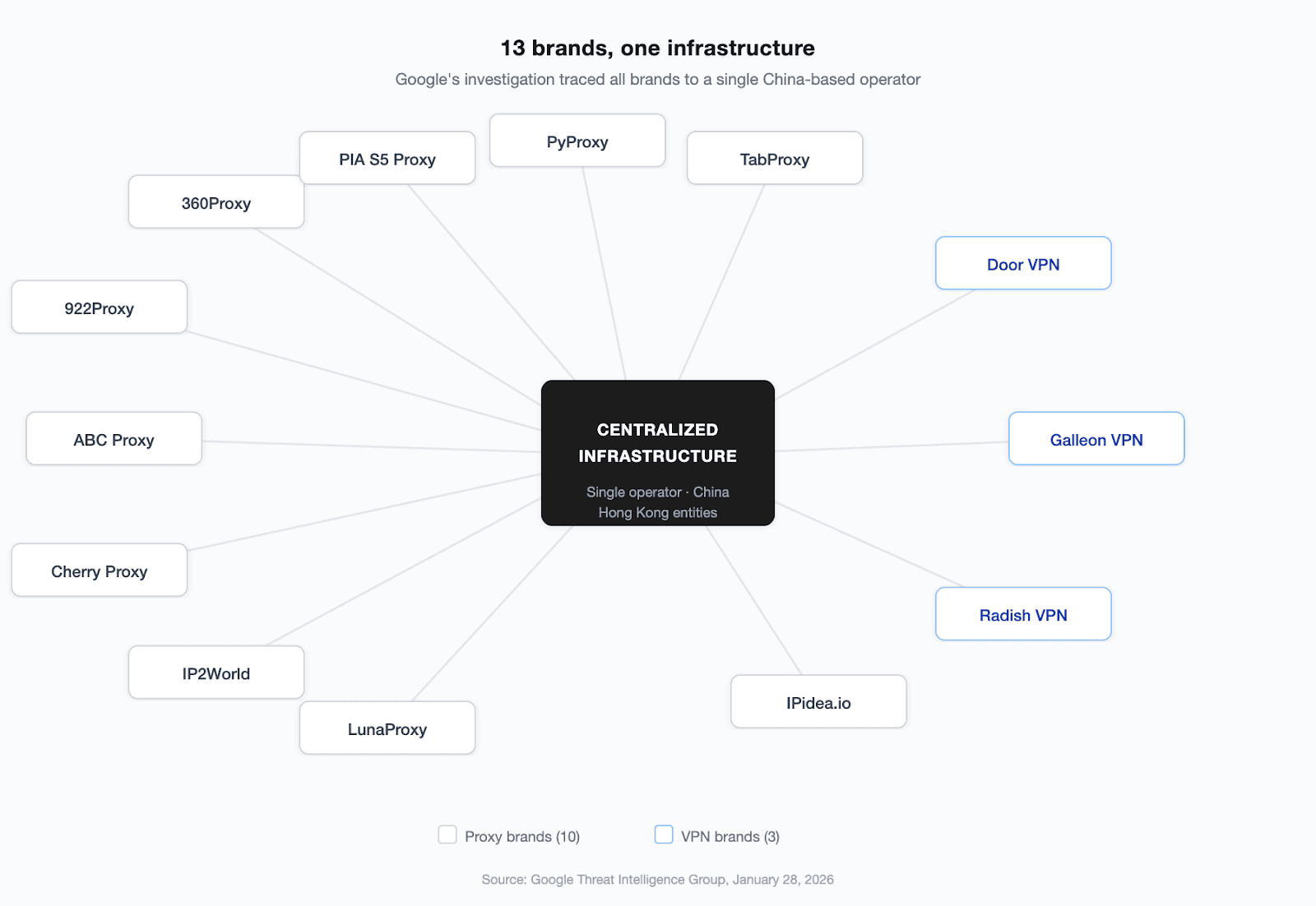
IPIDEA wasn't a single brand. Google's investigation found at least 13 proxy and VPN services controlled by the same operators:
360Proxy, 922Proxy, ABC Proxy, Cherry Proxy, IP2World, LunaProxy, PIA S5 Proxy, PyProxy, TabProxy, Door VPN, Galleon VPN, Radish VPN, and IPidea.io.
All of them routed through a centralized infrastructure managed by a single group based in China, incorporated through Hong Kong entities. Between 2022 and 2024, over 20 Hong Kong-incorporated entrants entered the proxy market with "unlimited" plans at prices that undercut legitimate providers.
How did the network recruit devices?
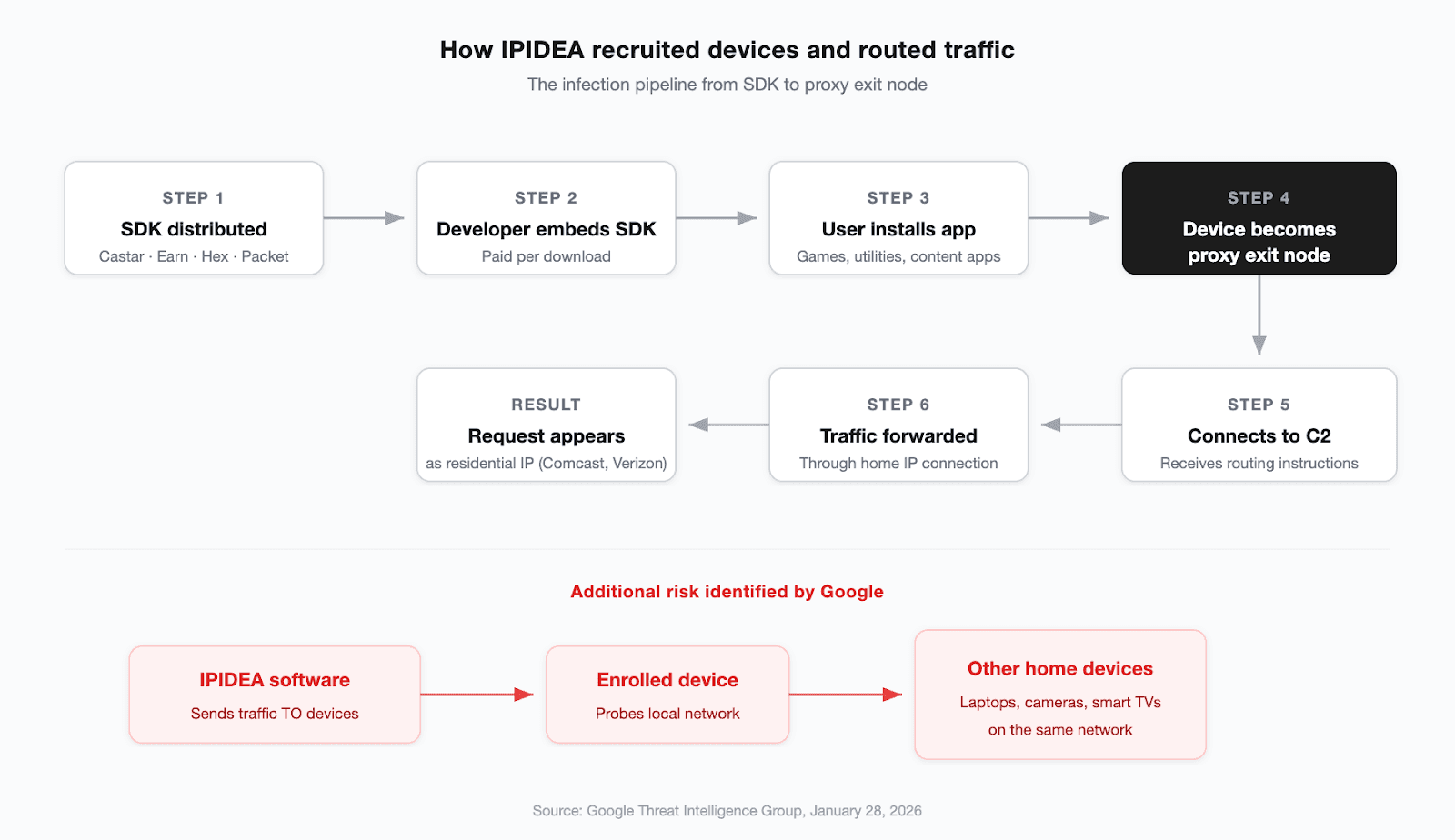
The infection pipeline centered on 4 SDKs (Castar, Earn, Hex, and Packet) marketed to app developers as a monetization tool. Developers who embedded the SDK were paid per download. The SDKs supported Android, Windows, iOS, and WebOS.
When a user installed an app containing one of these SDKs, the device became a proxy exit node. The app continued working normally: games, utilities, content apps, regardless of its stated function. In the background, the SDK connected to a command-and-control infrastructure, received routing instructions, and began forwarding third-party traffic through the device's home internet connection. Google found that all 4 SDKs shared the same backend infrastructure despite operating under different brand names, which was one of the key indicators that connected the brands to a single operator.
A proxy customer's request would then appear to originate from a regular household IP, like a Comcast line in Ohio or a Verizon connection in Florida. That IP-level obfuscation was the core product IPIDEA provided.
Google's analysis identified an additional risk: IPIDEA's software didn't just route traffic through enrolled devices. It sent traffic to them, actively probing the local network. Research into the Kimwolf botnet showed attackers exploiting vulnerabilities in IPIDEA's own infrastructure to reach other devices on the same home network: laptops, cameras, smart TVs, or anything else sharing the same local connection.
Some devices didn't require a malicious download. Google found uncertified Android TV boxes that shipped from the factory with IPIDEA proxy payloads pre-installed.
Who was using the network?
During a single 7-day window in January 2026, Google observed over 550 tracked threat groups routing traffic through IPIDEA exit nodes. The list included APT28 (Russian GRU military intelligence), Sandworm (the GRU unit behind the NotPetya attack), Volt Typhoon (Chinese state-sponsored, targeting US critical infrastructure), and groups tied to North Korea and Iran.
The notable detail in Google's findings is the concentration: 550+ groups, in a single week, all routing through the same underlying infrastructure.
IPIDEA's SDKs also directly enabled 3 major botnets: BadBox 2.0 (which reached over 10 million enrolled devices), Aisuru, and Kimwolf. The SDKs recruited the devices; IPIDEA's proxy infrastructure gave threat actors the routing layer to control them.
Activities ranged from accessing victim SaaS environments to password spray attacks against enterprise infrastructure, all masked behind IP addresses that resolved to residential ISP ranges.
If your proxy provider was reselling IPIDEA pool access, your production scraping traffic was sharing exit nodes with state-sponsored espionage operations. Even if your work was entirely legitimate, your IP addresses were potentially flagged, your requests associated with malicious activity, and your infrastructure dependent on a network that could be disrupted at any time, as it was on January 28.
How did the takedown work?
Google's disruption combined legal action (court orders seizing command-and-control and marketing domains across all IPIDEA brands), DNS disruption through Cloudflare, platform enforcement via Google Play Protect (which now auto-removes apps containing IPIDEA SDKs on certified Android devices), and intelligence sharing with law enforcement and security researchers.
The result: IPIDEA's device pool shrank by millions. Multiple associated brand websites, including LunaProxy and ABC Proxy, went offline. Because proxy operators commonly share device pools through reseller agreements, Google expects cascading downstream impact on affiliated providers that were reselling IPIDEA's access under other names.
What do pool size numbers mean?
IPIDEA advertised 6.1 million daily IPs. That number was accurate in a limited sense; it reflected the count of compromised devices checking in on any given day.
But it said nothing about quality. Those 6.1 million addresses included devices that cycle offline, apps that get uninstalled, IPs already flagged by threat intelligence feeds, and addresses shared across 13+ brands and hundreds of paying customers. On any given request, you might have been routed through the same IP that APT28 used an hour earlier.
This is a broader problem in the proxy market. When a provider advertises "50 million IPs" or "100 million residential endpoints", they're typically counting every device that has ever connected to their network. This includes IPs that haven't been active in months, IPs flagged due to other customers' activity, and addresses cycling through dozens of users daily.
The more useful question is how many IPs are clean, active, and available for dedicated access right now. If a provider can't answer that specifically, the pool size figure is a marketing number, not an operational one.
It's worth asking about IP isolation and whether you can get exclusive use of your IPs rather than sharing a pool. A smaller set of clean, dedicated IPs will typically deliver better success rates at scale than a massive pool with unverified sourcing and no isolation between customers.
How do you verify what you're paying for?
These checks can be run independently on any proxy pool. These are the same tests we use internally when evaluating IP blocks, and they take minutes. They're worth running even on a trusted provider.
Fraud score check. Run IPs through detection APIs like Spur, IPQualityScore, or Scamalytics. Genuine residential and ISP-tagged IPs typically score low. High fraud scores suggest datacenter IPs that have been relabeled, or addresses from compromised devices already flagged by threat intelligence.
Reverse DNS lookup. Real ISP IPs resolve to hostnames belonging to actual service providers like Comcast, Verizon, AT&T, and Frontier. Datacenter IPs resolve to hosting companies like AWS, DigitalOcean, or OVH. If your "residential" proxy resolves to a cloud host, it's not residential.
Geolocation consistency. Residential IPs are associated with a relatively stable physical location. If the same IP appears in Texas one request and Germany the next, it's a rotating pool of devices. That inconsistency is exactly the kind of signal anti-bot systems detect.
ASN (autonomous system number) verification. Legitimate ISP proxies belong to ASNs owned by real internet service providers. Compare the ASN with the organization field. Mismatches indicate relabeled or misattributed IPs.
WebRTC (Web Real-Time Communication) and DNS leak testing. Check for leaks that expose the real IP behind the proxy, and verify that DNS queries route through the proxy path rather than leaking to your local resolver.
You can run most of these checks using free online tools. We built a proxy checker that handles fraud scoring, ASN and network identification, geolocation, DNS and WebRTC leak detection, and speed testing in a single pass. No account required.
What does the industry need to do now?
Google's report also characterized the residential proxy market itself as a "gray market that thrives on deception, hijacking consumer bandwidth to provide cover for global espionage and cybercrime". This characterization comes from Google's Threat Intelligence Group, backed by a multi-year investigation and a federal lawsuit.
Verifiable sourcing needs to become the standard. "Ethically-sourced" has become a marketing term with no enforcement mechanism. Providers should be able to show where their IPs come from, name the ISP partnerships behind their address blocks, and demonstrate that no device on their network was enrolled without informed consent.
Buyers should expect specific answers. Where do your IPs come from? Do you own your infrastructure or lease pool access? Can you show the ISP agreements behind your IP blocks? Can I get dedicated, isolated access? These are baseline questions. A provider with owned infrastructure can answer them with specifics. Vague responses about "partnerships" or "ethical sourcing" without naming ISPs or showing ASN data warrant scrutiny.
ISP proxies work differently from residential proxies at a structural level. Instead of harvesting bandwidth from consumer devices through SDKs or apps, ISP proxies are IP addresses assigned directly by internet service providers through commercial agreements. The IPs sit on servers in data centers but are registered to ISPs, so they carry residential-grade trust scores without depending on enrolled consumer devices. The sourcing problem that enabled IPIDEA doesn't apply to this model.
HypeProxies has a clear position here, and we have a stake in this conversation: we build ISP proxy infrastructure as a structural alternative to the IPIDEA model. Our ISP partners are Tier 1 carriers: AT&T, Frontier, and RCN. The IPs are assigned through commercial agreements, registered, and traceable, with no SDKs embedded in consumer apps, no harvested bandwidth, and full transparency on sourcing.
We also own and operate the physical infrastructure (the servers, the network routing, the transit capacity) in Tier 1 data centers. This is a deliberate choice. It means more work (late-night maintenance, physical hardware management) but it also means no dependency on third-party cloud infrastructure and no shared pools where our customers' traffic mixes with unknown actors.
We recently deployed 100,000 ISP-tagged IPs, 100 Gbps of internet transit, and 30 dedicated physical servers for a single enterprise data team. Dedicated machines, no shared tenancy, capacity provisioned at deployment. Across our full network, we handle over 60 billion requests monthly on static infrastructure. That volume depends on the underlying IPs being clean and the routing staying stable.
When Proxyway independently benchmarked our ISP proxies in their 2025 testing, our proxies recorded the fastest response time in their ISP proxy synthetic benchmarks, with perfect uptime across a 7-day, 70,000-request test.
We focus specifically on US-based static ISP proxies, and the performance numbers reflect it. We don't position ourselves as a global rotating residential provider covering 190 countries. For teams that need high-performance, clean US IPs for web scraping, retail monitoring, SEO, or automation at scale, that specialization supports consistent performance.
Immediate action list
If you're on any brand identified by Google as IPIDEA-affiliated (including 360Proxy, 922Proxy, ABC Proxy, Cherry Proxy, IP2World, LunaProxy, PIA S5 Proxy, PyProxy, TabProxy, or any provider that recently went offline), migration should be the immediate priority. According to Google's investigation, traffic through these services was routing through malware-enrolled consumer devices.
If you're confident in your current provider, it's still worth running the verification checks above. Google's investigation showed brands marketed as independent were reselling the same compromised pool under different names. The overlap may be wider than currently understood.
If you're a developer, this warrants an audit of third-party SDKs in your applications. The IPIDEA-specific SDKs are known, but the underlying business model (pay developers per download, enroll devices without user consent) could be replicated by other operators.
If you're evaluating new providers, start with the basics: ISP partner names, ASN data, infrastructure ownership details. Test the IPs yourself before committing, and give more weight to infrastructure quality and IP cleanliness than to pool size numbers.
Where does this leave the market?
Google's report explicitly warns that the residential proxy market is expanding rapidly, with significant overlaps across providers. IPIDEA was one of the largest networks disrupted so far. It's unlikely to be the last.
For data teams running scraping pipelines, price monitoring, market research, or training data collection, it reduces to a practical question: is your proxy infrastructure built on something that will hold up when the next gray-market network gets taken down?
The providers that remain operational through these disruptions are the ones with verifiable ISP relationships, owned infrastructure, and IP addresses that can be independently audited. We've built HypeProxies on this model for 7 years, and the IPIDEA takedown is a concrete illustration of why it matters.
If you want to audit your current setup, the proxy tester is free, no login required. If you need infrastructure for production-scale data operations, you can reach our team on Discord to discuss whether our setup fits your use case, and we'll say so directly if it doesn't.
Related reading from our blog:
ISP Proxies vs. Residential Proxies: A Head-to-Head Comparison: a deeper look at the technical and operational differences between the two proxy types discussed in this article.
Best Proxies for Web Scraping in 2026: The Economics of Ownership vs. Renting: why infrastructure ownership matters for teams running data collection at scale.
Share on
$1 one-time verification. Unlock your trial today.
Stay in the loop
Subscribe to our newsletter for the latest updates, product news, and more.
No spam. Unsubscribe at anytime.





